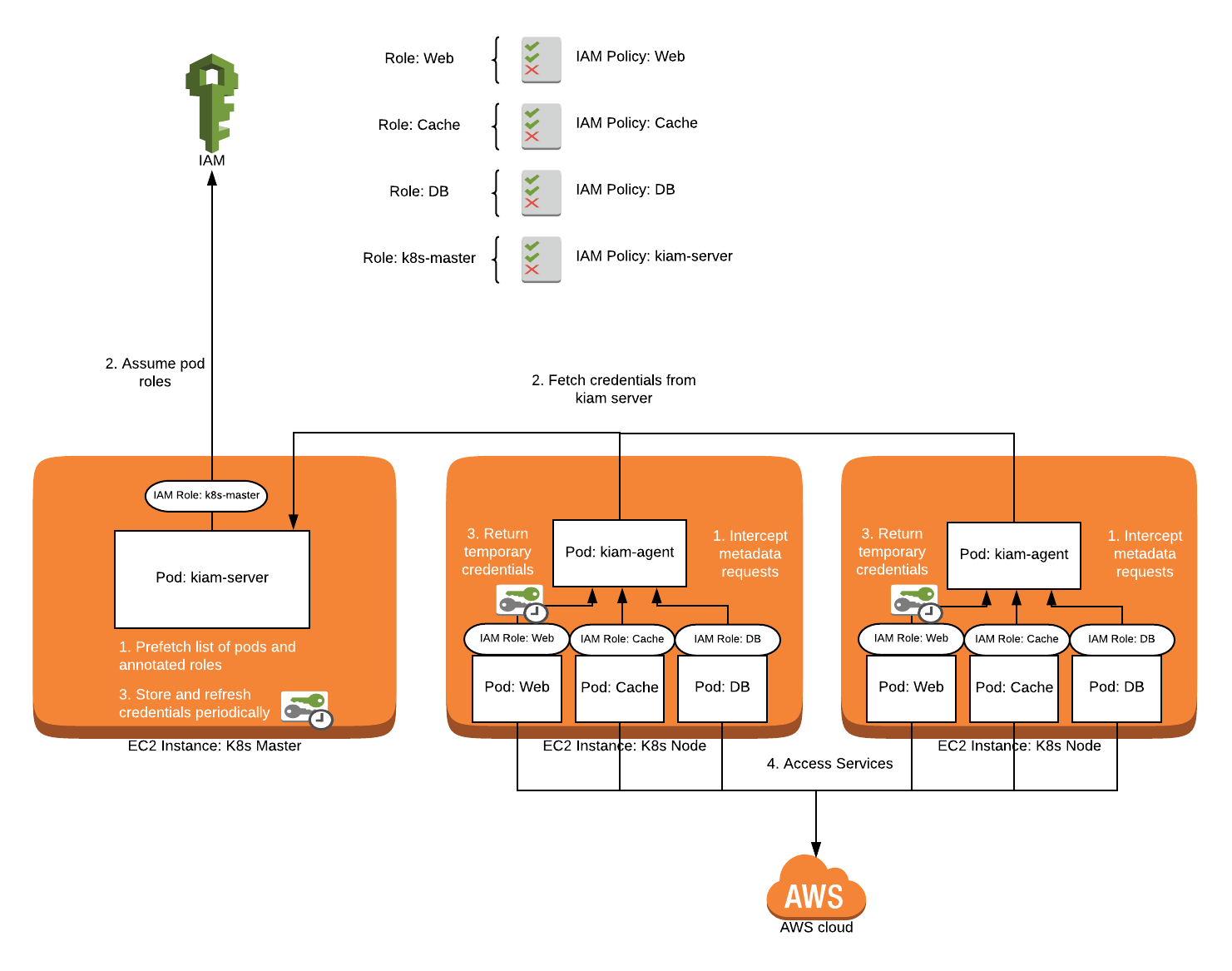
An overview of the will.iam architecture and its authorization workflow. | Download Scientific Diagram

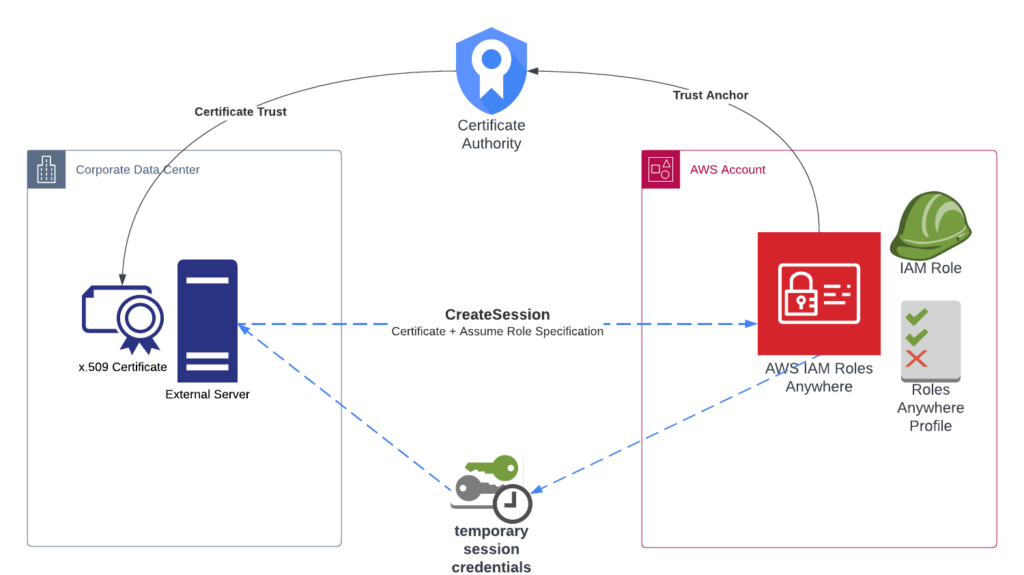
Securing AWS Log Transfers from On-Premises Servers: A Comparative Guide on Using IAM Roles vs. User Credentials with Fluent Bit
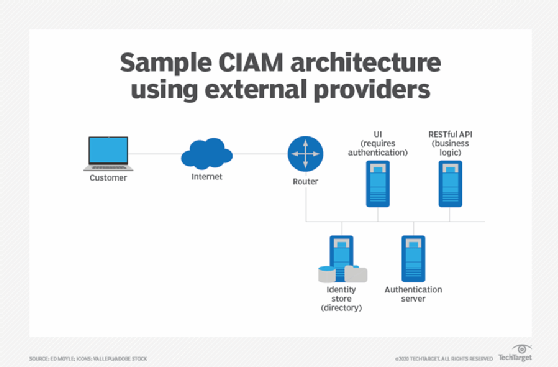
About using Amazon IAM roles with NetBackup | About the cloud storage | Veritas NetBackup™ Cloud Administrator's Guide | Veritas™